Tech Magazines
Mobile-Enabling Your Workforce with Apps You Already Have
Get this free Magazine
Learn how you can unlock your legacy IBM mainframe and midrange assets and make them seamlessly accessible to your mobile audience.Request Free! Get this free Magazine

Press Release Distribution in KSA/GCC/MENA
Lastest Tech Magazines
Exploit Kits: Cybercrime's Growth Industry
Get this free Magazine
Cybercriminals have turned their attention away from exploiting Windows operating systems to pursuing the popular third party applications installed on…
Mainframe Applications and the MQ-Enabled Multi-Tier World
Get this free Magazine
This solution brief evaluates the need for MQ-enabling COBOL applications as a path to service enablement. It also presents a…
Mainframe Service Enablement: How Attachmate Gets You There
Get this free Magazine
This two-page solution brief focuses on the mainframe challenge and the importance of using standards-based technologies in any integration project.Request…
Tmux Cheat Sheet
Get this free Magazine
Well, you might be thinking, “hey, I can just open up multiple terminal windows or open up multiple tabs in…
Installing an SSL Certificate on CentOS Running Apache(Let's Encrypt Project Instructions)
Get this free Magazine
You will: Start out by installing Apache with mod_ssl. From there, you’ll add firewall rules to allow HTTP and HTTPS…
Coding Projects
Get this free Magazine
In this resource you will find links to over one thousand computer programming project ideas. Use this list to hone your…
Man Page Cheat Sheet
Get this free Magazine
All the answers are in the built-in man pages on a Linux system! That’s probably not what you wanted to…
Find Command Cheat Sheet
Get this free Magazine
The options determine whether find will follow symbolic links (symlinks) as if they are the files they reference. One or…
Get Free Tech Magazines
Mobile-Enabling Your Workforce with Apps You Already Have
Get this free Magazine
Learn how you can unlock your legacy IBM mainframe and midrange assets and make them seamlessly accessible to your mobile audience.Request Free!…
Exploit Kits: Cybercrime's Growth Industry
Get this free Magazine
Cybercriminals have turned their attention away from exploiting Windows operating systems to pursuing the popular third party applications installed on nearly every…
Top 6 Cost Considerations When Evaluating A Cloud Service
Get this free Magazine
For business applications, not all clouds are created equal. Making the wrong choice could lead to a loss of revenue, productivity, reputation…
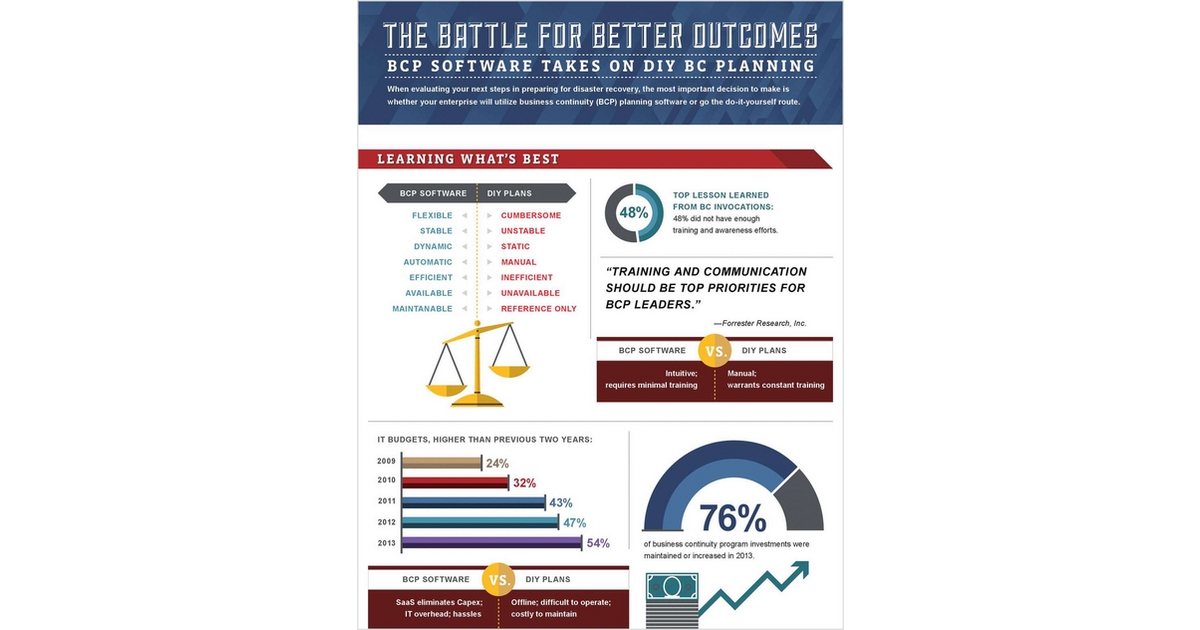
BCP Software vs. DIY: How to Make the Most Important Decision in Business Continuity Planning
Get this free Magazine
Learn why and what you need to take into account to ensure resiliency by downloading this infographic. We take a revealing look…