Security
PowerShell Security eBook
Get this free Magazine
Control execution of scripts using execution policy, code signing and constrained language mode Secure PowerShell remoting with SSH und TLS Delegate administrative tasks with JEA Audit and analyze PowerShell activities,…

Press Release Distribution in KSA/GCC/MENA
Lastest Security
ChatGPT is Trending
Get this free Magazine
ChatGPT is a hot topic trending across every industry. Gaps are being left open for cyberattacks, with many possibilities for improvement. We’ve pulled…
Data Protection and UCaaS Investment: India
Get this free Magazine
India’s political leaders are set to re-introduce the oft postponed Data Protection Law in the Budget session of the Parliament…
The Promise and Reality of Cloud Security
Get this free Magazine
The shift to remote work during the COVID-19 pandemic and digital transformation projects have moved cloud infrastructure front-and-center as enterprises…
7 Key Takeaways to Passwordless Authentication
Get this free Magazine
Passwords represent an ongoing security threat for companies. Research suggests that over 80% of data breaches are due to weak…
What Is The Most Secure Mobile Operating System?
Get this free Magazine
We’ve already established that your smartphone needs good security software to battle an array of hacks and flaws, but which…
12 Tools You Can Use to Help Beat Ransomware
Get this free Magazine
Antivirus software is a continually evolving market. It has to be both proactive and reactive to mitigate new and existing…
Get Free Tech Magazines
Exploit Kits: Cybercrime's Growth Industry
Get this free Magazine
Cybercriminals have turned their attention away from exploiting Windows operating systems to pursuing the popular third party applications installed on nearly every…
Top 6 Cost Considerations When Evaluating A Cloud Service
Get this free Magazine
For business applications, not all clouds are created equal. Making the wrong choice could lead to a loss of revenue, productivity, reputation…
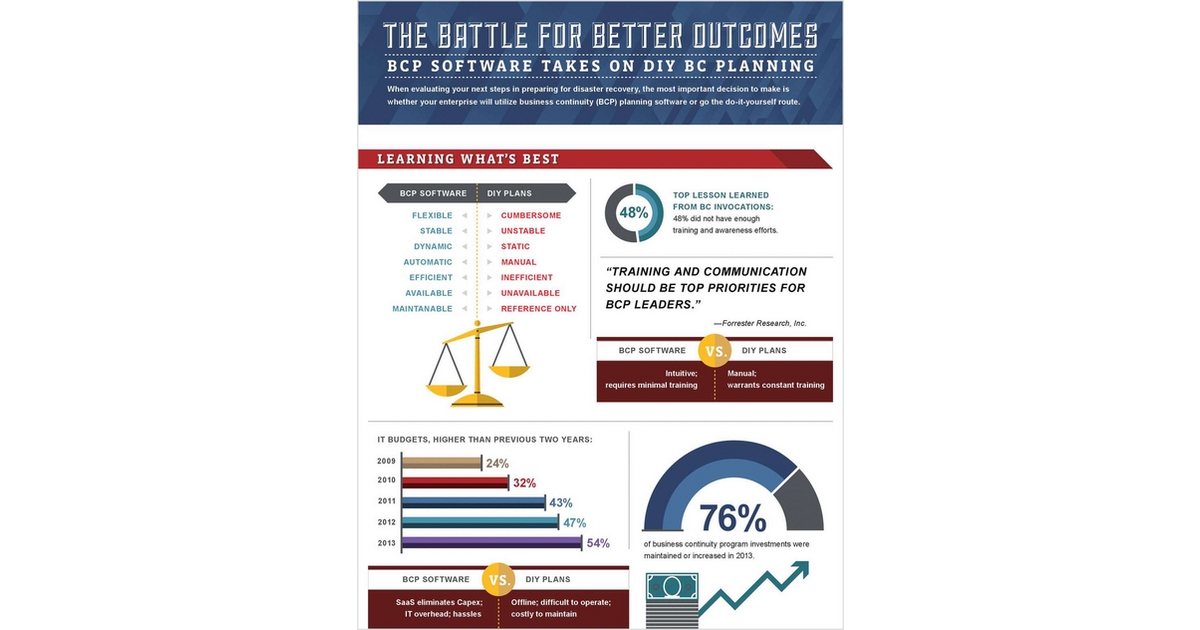
BCP Software vs. DIY: How to Make the Most Important Decision in Business Continuity Planning
Get this free Magazine
Learn why and what you need to take into account to ensure resiliency by downloading this infographic. We take a revealing look…
Explore How Paul VI Catholic High School Benefited From Fujitsu's Devices and Software
Get this free Magazine
Paul VI Catholic School wanted to develop a laptop program that would equip its students and teachers with the right tools to…